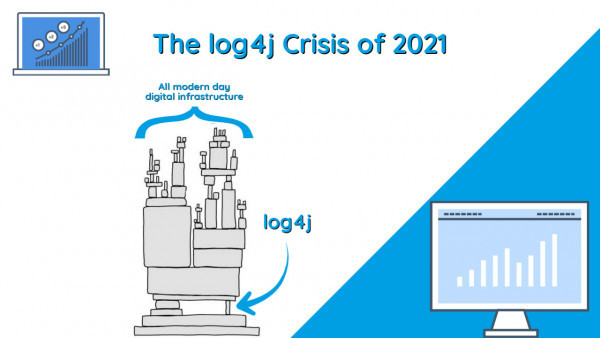
Let’s first give you in non-techy speak what log4j is. Its code – a series of numbers, letters and symbols used to help software and apps keep track of past activities. Similarly, to how Word keeps track of the changes you’ve made to a document, and you can hit a command to undo or redo the change. The difference is that log4j is free to use on the internet, its open source and widely used, this is where we can run into issues.
What is the issue with log4j?
Seems like a great piece of code, right? Nothing could go wrong. Just a few weeks ago an online group of cybersecurity experts discovered something. They discovered that when log4j was asked to log something new – it would also execute code in the process. Malicious code was run in the same scenario – and the log4j while trying to figure it out, ran that code. Now servers are susceptible to hackers and bad actors. Simply by sliding a bad line of code into log4j’s interface.
This sounds simple to do, really it does take a hacking professional to achieve, but that doesn’t mean it hasn’t been tried in many organizations with servers around the world.
Experts also say that this is the largest software vulnerability of all time in cyber security. The number of services and sites, servers and businesses that use log4j is insane. If you haven’t already contacted your IT provider to make sure you have done any patches or updates to ensure your organization cannot be hacked.
If you are a ‘non-technical mind’ and are still struggling to understand this don’t worry. We have a better explanation. We realize the amount of highly technical people that post to blogs and understand that not everyone is a graduate from computer science.
Just imagine all the houses on your street had the same type of lock. And suddenly, they all stopped working. Not saying the entire world is going to be hacked – but the issues with log4j certainly made it way easier to do so.
If your kids or you play Minecraft – in that software, there is a chat feature. You simply copy and paste a malicious line of code into the chat – and log4j does the rest. People have even been changing their twitter handles to this type of malicious code.
We don’t suggest you try it. Overnight when this came out, programmers and experts spent hours finding patches and fixing things. Google itself had over 500 engineers going over code looking for vulnerabilities and making sure it is safe.
So, we can stop worrying about the larger companies and corporations. But what about you, the business with 10-100 employees? Who is protecting your servers and data from hackers?
That’s where Skycomp Solutions Inc. comes in! We identified the day the exploit was found that no vulnerable systems were exposed to the internet and posed a high risk. We also have developed some custom scripts to scan every machine to find potentially vulnerable systems and have been working through applied vendor recommended patches.
If you didn’t know Skycomp Solutions Inc is a Managed Service Provider – if you don’t know what that is, are you living under a rock? Just kidding – but read more about it here: What is a Managed Service Provider?
Thanks for reading and soaking up this knowledge about the log4j exploit – maybe the company you work for hasn’t done anything about it yet. You might want to warn someone before it’s too late.